source::https://arstechnica.com/security/2017/06/advanced-cia-firmware-turns-home-routers-into-covert-listening-posts/
Home routers from 10 manufacturers, including Linksys, DLink, and Belkin, can be turned into covert listening posts that allow the Central Intelligence Agency to monitor and manipulate incoming and outgoing traffic and infect connected devices. That's according to secret documents posted Thursday by WikiLeaks.
Home routers from 10 manufacturers, including Linksys, DLink, and Belkin, can be turned into covert listening posts that allow the Central Intelligence Agency to monitor and manipulate incoming and outgoing traffic and infect connected devices. That's according to secret documents posted Thursday by WikiLeaks.
CherryBlossom, as the implant is code-named, can be especially effective against targets using some D-Link-made DIR-130 and Linksys-manufactured WRT300N models because they can be remotely infected even when they use a strong administrative password. An exploit code-named Tomato can extract their passwords as long as a default feature known as universal plug and play remains on. Routers that are protected by a default or easily-guessed administrative password are, of course, trivial to infect. In all, documents say CherryBlossom runs on 25 router models, although it's likely modifications would allow the implant to run on at least 100 more.
WikiLeaks
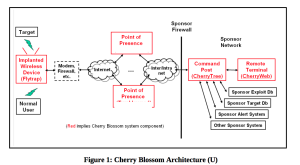
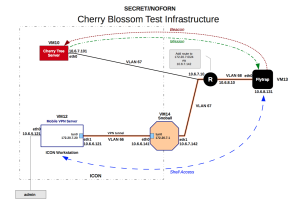
The 175-page CherryBlossom user guide describes a Linux-based operating system that can run on a broad range of routers. Once installed, CherryBlossom turns the device into a "FlyTrap" that beacons a CIA-controlled server known as a "CherryTree." The beacon includes device status and security information that the CherryTree logs to a database. In response, the CherryTree sends the infected device a "Mission" consisting of specific tasks tailored to the target. CIA operators can use a "CherryWeb" browser-based user interface to view Flytrap status and security information, plan new missions, view mission-related data, and perform system administration tasks.
Missions can target connected users based on IPs, e-mail addresses, MAC addresses, chat user names, and VoIP numbers. Mission tasks can include copying all or only some of the traffic; copying e-mail addresses, chat user names, and VoIP numbers; invoking a feature known as "Windex," which redirects a user's browser that attempts to perform a drive-by malware attack; establishing a virtual private network connection that gives access to the local area network; and the proxying of all network connections.
WikiLeaks
All the communications between the FlyTrap and the CIA-controlled CherryTree, with the exception of copied network data, is encrypted and cryptographically authenticated. For extra stealth, the encrypted data masquerades as a browser cookie in an HTTP GET request for an image file. The CherryTree server then responds to the request with a corresponding binary image file.
A decade of hacking routers
In many respects, CherryBlossom isn't much different from DNSChanger and other types of router malware that have infected hundreds of thousands of devices over the past few years. What sets the CIA implant apart the most is its full suite of features, including its user interface, command-server support, and a long list of mission tasks. Also significant: the documents date back to 2007, when router hacking was less developed than it is now.
CherryBlossom is the latest release in WikiLeaks Vault7 series, which the site purports was made possible when the "CIA lost control of the majority of its hacking arsenal." CIA officials have declined to confirm or deny the authenticity of the documents, but based on the number of pages and unique details exposed in the series, there is broad consensus among researchers that the documents are actual CIA materials.
What's more, researchers from security firm Symantec have definitively linked at least one Vault7 release to an advanced hacking operation that has been penetrating governments and private industries around the world for years. While WikiLeaks said Vault7 was intended to "initiate a public debate about the security, creation, use, proliferation, and democratic control of cyberweapons," little or nothing published to date has shown the CIA running afoul of its legal mandate.
Like the other Vault7 releases, Thursday's installment doesn't include the source code or binaries that would allow other hacker groups to appropriate the CIA's router-hijacking capabilities. That makes the leaks significantly less damaging than those by the Shadow Brokers, the name used by a still-unknown group that has been published advanced hacking tools developed by and later stolen from the National Security Agency. April's release of an NSA-developed tool codenamed EternalBlue resulted in the WCry outbreak that infected an estimated 727,000 computers in 90 countries.
Thursday's Vault7 release does, however, provide so-called indicators of compromise that targets can use to determine if they were hacked. As pointed out by a researcher who tweets under the handle Xorz, it may allow people to identify CIA-controlled CherryTree servers, since they all seem to use the word "CherryWeb" in their default URLs.
A general defense more technically inclined users can take against router-based malware that monitors and tampers with Internet traffic is to put the router in question into passive mode and connect it to network hub and a trusted router. This allows the person to see all traffic going into and out of the network.
Comments
Post a Comment